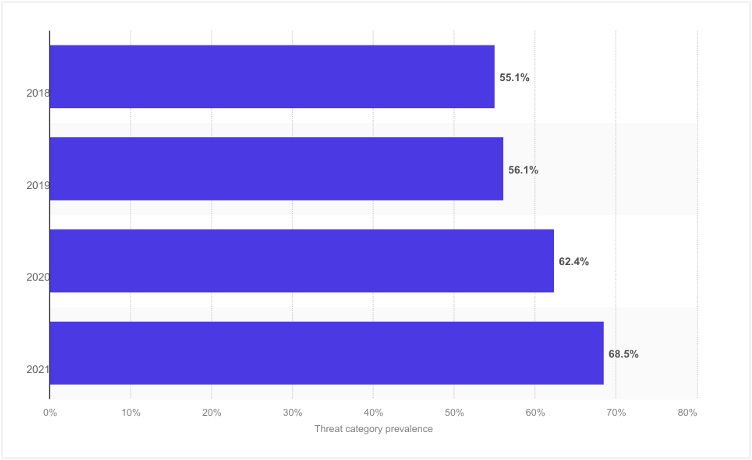
Ransomware attack cases are on a steady rise across the globe. According to a 2021 study, 68.5% of businesseswere victims of ransomware. This marked an alarming increase from previous years, with 2021 recording the highest ransomware attacks.
Ransom attacks are not going away; therefore, it’s paramount for companies to rethink their strategies around ransomware attacks. If not dealt with appropriately, companies risk losing millions of dollars in revenue. According to a 2021 report, data breaches cost companies an average of $4.24 million, the highest cost in 17 years. Such figures indicate that data breaches will only get costlier if companies do not take appropriate measures to protect their enterprises.
Below are ways to detect ransomware and how to take appropriate measures to protect your organization.
What is Ransomware?
Ransomware is encrypted malware that penetrates IT systems to hold user information at ransom. This type of malware works by encrypting a user’s data not to access their files, then demands a ransom, so the user gets access again. Cybercriminals gain entry into a company’s IT systems by releasing encrypted ransomware. This malware spreads across devices and applications. Most ransomware blocks access to your company’s IT assets, erases or encrypts files in the compromised system.
How Does Ransomware Work?
Cybercriminals generally spread malware through user actions, like downloading a suspicious file or clicking a harmful link. Phishing attacks are the most common delivery methods for ransomware. For example, a user could unknowingly download a dangerous file from an unknown email that proceeds to encrypt their documents.
How does a ransomware attack work? Once the user downloads and opens the file, the ransomware takes over their device and quickly infects all their files. In other instances, the ransomware tricks users into giving them admin access where the attackers can fully manipulate the device.
The only way to re-access your files is by requesting a unique key from the attacker who demands a ransom in exchange for the key. Some ransomware comes embedded with social engineering software to trick users into giving credentials and admin access. Other types of ransomware exploit security loopholes without needing input from the user.
At this point, the attacker encrypts the user’s files then demands a “fine” in cash payment or cryptocurrency. Often, attackers disguise themselves as law enforcement personnel who claim the user possesses copyrighted information or sexually explicit content. This scare creates panic in the user and forces them to pay them since they most likely will not report the incident to authorities.
Another method that ransomware criminals use is by threatening the user that they’ll leak confidential content from their device. Fear of revealing sensitive information forces the user to pay the ransom out of publicizing personal information.
The ransom payment period ranges between 24-48 hours because attackers are trying to maximize financial gain without getting caught.
How to Detect Ransomware?
How does a ransomware attack work? Detecting ransomware is sometimes tricky. Users often notice the attack long after the cybercriminal breached the system. Here’s how to check ransomware attack in pc systems and prevent them from diffusing across the company’s network.
- Unusual activity within your file system, such as a large number of files created or deleted anonymously due to a cybercriminal trying to access the files.
- Increased CPU and drive activity without your input, indicating that the attacker is trying to access your file system.
- Suspicious and repeated login activity. It’s normal for users to forget their passwords and try to log in to their accounts a couple of times. However, if there’s an unusual spike in login attempts, especially from different users, it’s likely from a potential attacker.
- Phishing emails and messages. Phishing is a favorite among ransomware attackers because it is easy to trick users into clicking harmful links or downloading attachments.
- Corrupted backup system. Attackers target your backup systems by disabling the security controls to get complete access to your backup up files. For you to gain access back to your backups, you’ll have to pay a ransom.
- You’ll notice a few devices have been encrypted, denying users access. If you encounter such a scenario, chances are attackers are testing their plan on a few devices before launching a full assault on your entire system.
- The presence of popular hacker software such as Microsoft Explorer, MimiKatz, PC Hunter, or GMER. Cybercriminals commonly use these tools for disabling security controls and. stealing personal identification information.
- Attempts to deactivate your Active Directory. Attackers do this by using remote software to break into Active Directory servers. Once bad actors break in, they install their ransomware into the domain controller logon script and proceed to infect anyone who logs into the Active Directory server.
- Suspicious network interactions between the attacker’s malware and their control and command server.

Types of Ransomware
There are five ransomware attack types common across all industries.
1. Crypto Ransomware
The goal of a crypto attack is to encrypt your files without interfering with your computer’s functionality.
A crypto attack is one of the most popular and damaging forms of ransomware because most users are often caught off guard without any backup.
Developers install a countdown in the malware to force users to pay to access their data. A famous example is the Locky ransomware, where the malware spread across an entire organization by encrypting more than 160 files.
2. Locker Ransomware
This ransomware disables your PC’s essential functions and locks the user from accessing their files, folders, and system settings. However, they can still control their keyboard and mouse. Attackers display a ransom demand screen so you can pay the price to gain back access to your computer. This type of attack rarely compromises your files compared to a crypto attack.
3. Scareware
This counterfeit software notifies the user of a potential virus attack in their computer and tricks them into paying to remove the malware. The user pays and ends up downloading harmful software or clicking on links that lead to untrusted websites. Some scareware tools lock your PC or flood your computer with pop-up windows that disrupt your computer’s performance.
4. Extortionware or Leakware
Also known as doxware, this type of ransomware coerces users to pay a ransom by threatening to leak sensitive information to the public. Most people pay a ransom out of panic and fear of personal information leaking to the internet.
A popular type of leakware is one that masquerades as law enforcement agencies. Attackers claim to have detected unlawful online activity such as possessing copyrighted information or sexually explicit content in your computer. The users end up paying a ransom due to fear of shame and exposure.
5. Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) is a pay-to-use malicious software service. RaaS developers create software then sell it to affiliates who use the malware to extort money or bitcoin over stolen data.
Previously, RaaS authors would directly use the software to encrypt data but now prefer affiliates who pay the developers a percentage of the stolen money.
Ransomware Attacks
Ransomware attack variations have grown due to cryptocurrency enabling attackers to hide money in untraceable currencies like bitcoin and ethereum. Additionally, cybercriminals are making money off user and company information thanks to the growth in data volumes. Some notable ransomware attacks in recent history are:
- Cerber was a RaaS software that bypassed Microsoft’s security systems and infected their networks. Attackers made away with USD 200,000
- Robbin Hood shutdown systems in Maryland, The City of Baltimore in 2019
- GandCrab was another lucrative ransomware attack that netted more than $2 billion in July 2019. The developers sold it to cybercriminals who used the malware to wire the money into their accounts
- The latest ransomware as a Service software is Thanos and was exposed in January 2020. This form of ransomware is sophisticated enough to circumvent popular anti-ransomware solutions
How to Defend Against Ransomware
The tips below are how to mitigate ransomware attacks:
- Develop a ransomware response plan that includes quick recovery tactics when users detect ransomware.
- Use backup systems that allow the saving of multiple backup iterations in case attackers infect some files. Implement two-factor authentication for accessing backup files and routinely test for safety and data integrity.
- Utilize malware protection software and always ensure to protect your systems with the latest version. Activate routine scanning and automate signature updates. Also, implement anti-phishing solutions to prevent harmful emails from getting into your company’s network.
- Add a warning sign to all external emails to notify users of harmful downloads and links. Utilize Microsoft Viewer tools to open Microsoft files sent through emails and deactivate macro scripts.
- Apply latest software patches to all your IT assets, including applications, operating systems, mobile devices, cloud infrastructure, PCs, printers, networking devices. Ensure the security controls are up to date and, if possible, use a centralized patch management solution.
- Implement blocklisting, allow listing, and greylisting policies to prevent ransomware execution in files and folders across your applications and software solutions.
- Use a proxy server to restrict unauthorized internet access. Also, limiting access to personal accounts and emails while on the company’s network.
- Monitor and vet third-party software and users who have remote access to your company’s systems. Ensure they adhere to your company’s security standards at all times.
- Educate your company’s stakeholders on social engineering tactics so they’re better prepared to detect ransomware attempts. Also, train them on how to create strong passwords. How to implement multi-factor authentication and how to identify phishing emails.
- Develop an automated remote plan that users can quickly report ransomware attempts.
- Restrict access to virtual computing infrastructure and remote desktops to authorized users.
- Embrace zero-trust policies and always vet users’ activity within your company’s network. Communicate to all stakeholders that admins continuously monitor their activity while connected to the company’s network.
How to Respond to a Ransomware Attack
If your systems are already compromised, here’s how to deal with ransomware attack attempts and what to do with ransomware attack scenarios:
- Immediately disconnect all devices and accounts from the network to prevent further damage
- Check if the ransomware has a decryptor. In some rare instances, it’s possible to decrypt your files and get them back from the attacker without paying a ransom.
- Do not pay any ransom to cybercriminals. Instead, activate your backed-up assets, so the business continues, then report the matter to cyber security professionals.
- The problem with paying ransom to bad actors is that there’s no guarantee you’ll get your assets back. Furthermore, by paying the ransom, you strengthen their mission and increase your chances of getting attackers again.
- Isolate affected endpoints and user accounts and remove them from your network. Isolating prevents attackers from spreading their malware to the rest of your IT environment.
- Deactivate automated maintenance activities on affected systems to allow investigators to get to the root cause.
Partner With Experts in Cybersecurity
Keeping one step ahead of the continually evolving threat landscape is a full-time activity and requires specialist knowledge and skillset. Many smaller organizations do not have dedicated resources or a budget to hire security experts. Relying on a trusted partner in cybersecurity is a proven, cost-effective alternative. CG Technologies have over 25 years of experience delivering exceptional services to 100’s of companies in the Greater Toronto Area. Our managed cybersecurity services take care of your IT security needs allowing you to focus on your business’ growth. We’ve designed our security services and solutions around the problems and obstacles that face small to medium businesses every day. Download our whitepaper, the small business guide to ransomware protection or contact us to arrange a security assessment before a security breach or ransomware attack impacts your business.
