Your firewall is the first line of defence between your computer systems and public networks, so it makes sense to conduct rigorous firewall audits regularly. Furthermore, if you have an environment with firewall solutions from multiple vendors with different rules, you need a standardized checklist to fulfil your firewall configuration audit according to government regulations and cybersecurity policies.
This article explores the firewall audit checklist and the types of firewalls ideal for your company.
What is a Firewall?
A firewall is a network security software or device that filters inbound and outgoing network traffic. The firewall uses a set of security rules to allow or block access to a private network.
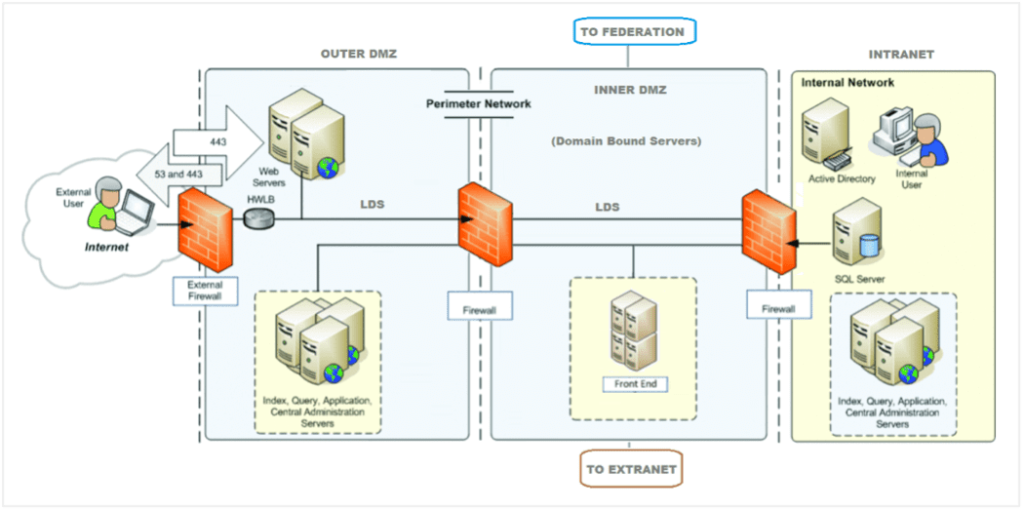
(Image source: att.com)
In essence, a firewall acts as a security barrier between your IT environment and external networks to block unauthorized users and malicious software. That way, you protect your IT assets from cyberattacks and unwanted traffic.
There are different types of firewall protection, and each level depends on the amount of security you need. Let’s explore the types of firewalls.
Types of Firewall
There are multiple types of firewalls in the form of hardware or software tools. A hardware firewall is a physical device that filters and blocks traffic to and from your computer, while a software firewall does the same; the difference is that the software firewall filters network traffic through an application within the computer. So, with this definition in mind, below are the different types of firewalls:
Proxy Firewall
Proxy firewalls protect your network by filtering traffic at the application layer. Also known as a gateway firewall, it acts as a go-between in all network connections by controlling applications supported by a network and limits contacts to systems directly. A proxy firewall is more secure than other firewalls because it has its Internet Protocol Address (IP address), meaning external connections cannot receive data packets directly from your network.
Packet-Filtering Firewall
A packet-filtering firewall is the most basic type of network protection that works well in smaller networks. This form of firewall blocks port numbers, IP addresses, and IP traffic but does not filter web attacks. In addition, packet-filtering firewalls base their traffic filtering on port information and IP addresses, which is insufficient to detect malicious activity. Meaning, the packet-filtering firewalls are easily spoofed and are not ideal for large, complex networks.
Stateful Multi-Layer Inspection (SMLI) Firewall
The Stateful multi-layer inspection (SMLI) firewall uses a refined form of packet-filtering that monitors traffic in seven layers of the Open System Interconnection (OSI) Model. It combines stateful inspection, layer inspection, and packet-filtering technology to determine if packets are part of a recognized connection or not.
Unified Threat Management (UTM) Firewall
Considered an all-in-one firewall solution, Unified Threat Management firewalls are a sophisticated mix of hardware and software security tools. This mix comes as a unified interface that controls security with multiple security devices, software, rules, and policies. Additionally, a Unified Threat Management firewall is managed centrally through a dashboard that displays all security components. Standard features of a Unified Threat Management Firewall include:
- Virtual Private Network
- Gateway
- Web security
- Bandwidth Management
- Email filtering
- Routing capabilities
- Intrusion Prevention Systems
How does a Firewall Work?
A firewall works by analyzing network traffic based on a set of rules. The only traffic allowed has to meet the criteria configured into the security device or firewall software. The firewall does this by permitting or restricting specific packets, i.e., data sent through networks based on predetermined rules.
What is a Firewall Audit?
A firewall audit is a systematic process of identifying network vulnerabilities and reviewing existing firewall procedures to ensure they conform to security regulations and policies.
One of the main reasons companies conduct firewall audits is to conform to regulatory standards that govern cybersecurity. For example, the Payment Card Industry Data Security Standard (PCI-DSS) ensures that all organizations that process credit card information maintain secure computer systems.
Other standards relevant to a firewall configuration audit include the General Data Protection Regulation (GDPR) and the Sarbanes-Oxley (SOX) cybersecurity compliance standard.
Apart from meeting regulatory standards, firewall audits are a necessary practice to ensure security integrity across all your networks.

Firewall Audit Checklist
The firewall audit checklist contains an exhaustive collection of criteria to measure the effectiveness of your firewall practices. The list also helps you identify vulnerabilities within your networks. Below is a web application firewall audit checklist:
Gather Documents and Review Existing Firewall Policies
The first step in a firewall audit is to review your current security guidelines, rules, and policies. This should also examine any government and industry regulatory standards that pertain to your business operation and firewall security to ensure you are compliant with them.
Compare the policies against the regulatory standards that apply to your business to identify any misalignment. Details to collect for the audit process includes:
- Copies of firewall policies
- Access to firewall logs
- A visual representation of the current network
- Previous audit review documents
- A list of all VPNs and ISPs
- Firewall vendor data
- An understanding of all server and firewall setups
Review Specific Firewall Operations Guidelines
After reviewing the general policies and standards, move on to specifics. Next, an operational review looks at firewall management procedures such as approvals, accountability, and firewall changes.
Your company should also document policies for managing firewall compromises, the person responsible for handling security incidents, and how to engage law enforcement. Additionally, also review the communication plan to company stakeholders when security incidents affect business.
Review Firewall Authorizations and Administrators
Once you review the specific firewall management guidelines, the next step involves examining the people in charge of enforcing firewall policies. Questions to ask for this stage include:
- Are system administrators part of the firewall management team?
- Do they have the required training to manage firewall technology?
- Do they undergo routine training on firewall management?
- Is there a procedure for removing employee access when they no longer work in the company?
- What’s the process for removing members who no longer have firewall access privileges?
The answers to the questions above give you a clear picture of firewall administrators and their rights to make firewall changes.
Review Firewall Change Guidelines
Firewall change requests have to be handled systematically with the appropriate authorizations. Failure to track your change requests can result in costly security mishaps. To review your change procedures, these are the factors to consider:
- How to manage changes – document the procedure involved in receiving requests, tracking, approvals, and verification.
- Change authorizations – identify the person in charge of signing off change requests and whether there’s a formal process to getting approvals.
- Audit trail – identify the change request audit and accountability trail.
- Sample change requests – audit change requests and verify if personnel followed the documented process.
Review the Firewall Design
This involves reviewing the firewall technology the company uses, if it’s current and whether there’s a documented guideline for conducting firewall upgrades. Note that this procedure should capture both hardware and software firewalls. Also, look into security patches and if the firewalls get regular updates to remain current against potential threats.
Another critical component in firewall design review is the rules. Determine if the firewall’s rule base is adequate to control network traffic and protect the company.
Optimize the Firewall Rule Base
Identify and delete redundant rules and disable unused connections. Removing irrelevant restrictions ensures tight security and better firewall performance. Additionally, these are ways to optimize the firewall’s rule base:
- Evaluate the order of firewall rules to maximize security performance
- Delete unused objects
- Document rule changes
Risk Assessment
Risk assessment is essential in a firewall audit because you identify risk-prone rules and ensure the rule base complies with all standards and relevant regulations.
Plan for Ongoing Audits
After a successful audit and firewall configuration, ensure proper procedures for continuous security and compliance. Establish a schedule for conducting firewall audits and develop appropriate documentation of all policies
Why is a Firewall Audit Important?
A firewall audit helps in identifying system vulnerabilities and determining areas that need specialized attention. An audit also helps in streamlining firewall rules and improves its effectiveness in controlling network traffic.

Firewall audits are essential in continuously improving your company’s abilities to tackle malicious attacks as cybercrimes. Grow more sophisticated; it’s vital to update your firewall policies, rules, and procedures regularly.
