Identity and Access Management Policies & Compliance
What are IAM Identity-Based Policies?
Businesses measure IT’s effectiveness in identity and access management (IAM) based on their ability to provision access to systems, but IT professionals know there is far more to focus on when building an identity and access management compliance policy framework. Identity and access management policies begin with full data privacy and protection in mind and the realization that a robust identity and access management policy framework starts with securing systems and applications from intrusion and extends to the organization’s identity management and access policies for provisioning accounts.
 The identity and access management policy framework should start with documenting an approach to determining a user’s identity or organizational role and extend to provisioning access based on documented identity and access management policies. These policies generally document the access to be provided based on the person’s role in the organization. Once documented identity and access management policies are in effect, appropriate access can be requested and easily delivered based on the documentation.
The identity and access management policy framework should start with documenting an approach to determining a user’s identity or organizational role and extend to provisioning access based on documented identity and access management policies. These policies generally document the access to be provided based on the person’s role in the organization. Once documented identity and access management policies are in effect, appropriate access can be requested and easily delivered based on the documentation.
Essentially the documented identity and access management policies indicate and control the level of access to be granted for each system and application provided to the end-user, based on their organizational identity or role. Documenting the policies enables access to be granted manually and forms an important identity and access management policy template that can be used to implement automated provisioning systems that ensure identity and access management compliance.
Identity and Access Management Policies – Goal & Purpose
The most basic goal of identity and access management compliance is to ensure that authorized users have access to the information they need when they need it while preventing them from accessing information beyond their need. This also means preventing unauthorized users from gaining access to sensitive information.
There are three pillars for developing identity and access management policies:
- Confidentiality: Only appropriate individuals should be able to see data based on its sensitivity and privacy needs. Data is often classified as public, sensitive and/or confidential.
- Public data is that data that is available on websites and in the public domain.
- Sensitive data is generally information shared to employees but not available outside the organization.
- Confidential data is highly sensitive information that only certain people may access, based on a documented need to use that data while performing their day-to-day jobs.
- Availability: The two aspects of availability are making sure appropriate people have access to the information they need and that the systems and applications remain available to them so they may access the data. Denial-of-service (DDoS) or other external breaches can affect availability.
- Integrity: Above other concerns, data must be trustworthy, which can only be assured when access to data is fully secured. Just as denial-of-service attacks can affect the availability of data, security breaches can render it untrustworthy by calling its accuracy into question.
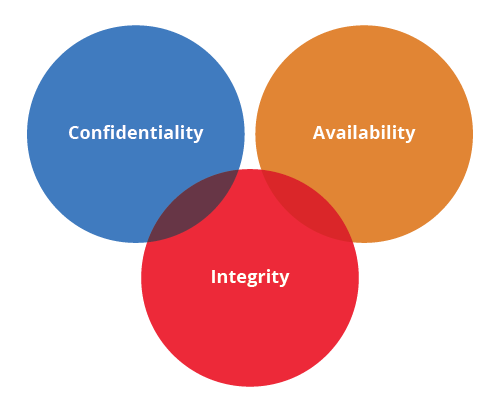
Robust identity and access management policies must address all three of these areas, beginning with securing the data centre and network on which applications run and extending into policies documenting how identity is established and access provided based on that identity. They should include a means of fraud prevention and extend to knowing when to remove access in the event of a change in role or job termination.
IAM Compliance Requirements
Identity and access management policies came under the microscope initially because of financial fraud and leading to the Sarbanes-Oxley Act of 2002 (SOX), but as Internet business has continued to grow, deliberate theft of data by bad internal actors and foreign influences have led to tighter compliance requirements over time. Every identity and access management policy framework should address IAM compliance requirements, including:
- Ability to prove sufficient controls demonstrating authorization and granting of access
- Separation of duties to ensure that the people granting access are not involved in authorizing it
- Protection of customer/consumer data, PII (personal identifying information), and PHI (personal health information)
- Responsibility for monitoring access to sensitive data and reporting it where required
- Provision of data based on "least privileged access" basis, meaning employees have access only to the minimum amount of information needed to do their jobs
- PCI compliance that requires limited employee access to customer credit cards and credit card information
- Data protection based on country of origin, dependent on international standards like GDPR
- Access Controls: Routine security audits must be performed demonstrating both the policies for gating and removal of access exist and that they are followed. When identity and access are managed manually, auditors will generally view access logs, selecting names at random and then requesting proof of authorization for the access that has been granted.
- Segregation of Duties: The best way to ensure proper segregation is to develop and implement an identity and access management policy template for each application, document the business owner and approval of access, and provide access. The policy should clearly demonstrate segregation: approvers should be embedded in business units, and access should be administered within IT.
- Access Monitoring and Reporting: This aspect of identity and access management compliance is required to ensure bad actors are not gaining access to private information and has become extremely sensitive recently due to reports of foreign governments tampering with elections and critical infrastructure. This requires products for intrusion detection and monitoring at the network's edges but also requires access to each application or datastore is tracked.
- Least Privileged Access: Identity and access management policies provide the documentation needed to prove least privileged access rules are developed and used within access administration. This is a fairly intensive area to develop: first, all sensitive data must be identified, and then roles that require access to it documented. Developing a matrix with these two data points will help organizations then develop the list of applications each role can access, the type of access they require (read/write) and document the identity and access management policies needed to govern provisioning.
- PCI, PII, and PHI Data Protection: Within the organization's identity and access management policy framework, the definitions covered by PCI, PII, and PHI must first be documented by an organization as different levels of compliance may be in effect for different types of organizations. Then the controls must be clearly called out and managed:
- Protection of data stores against external intrusion
- Processes used to prevent unintentional access
- Monitoring of access to data
- Local controls that ensure staff protect data
- Data Localization/Segregation (GDPR): GDPR and similar laws govern where data may be stored and who may have access to it. Global organizations need to be particularly careful as some countries require all personal data for their residents to be stored only in-country. This requires systems and data centres to be available locally. In contrast, other regulations simply require organizations to request certain permissions in the use of personal data.
Challenges in IAM Policies and Compliance Creation
With routine audits, the requirements to provide reports and notify people of breaches will be extremely challenging for certain types of organizations to demonstrate identity and access management compliance. The primary concern in almost every organization remains proving individual access follows policies and tying a person’s identity to their access, especially when access is managed manually. The challenge becomes even more significant when data can be accessed via personal devices and laptops with local hard drives.
Securing data from external intrusion is also challenging as it requires the ability to secure the data centre, network, and server/application environment. As systems become distributed amongst cloud servers, across multiple internal and externally hosted cloud infrastructure and globally diverse, the identity and access management compliance becomes even more challenging.
This leads to organizations wasting valuable resources meeting audit requirements, proving manual controls, monitoring systems for intrusion, and addressing security vulnerabilities and breaches. With as much effort as they are spending, many learn it’s still not enough when they fall prey to ransomware attacks, data breaches, or other denial of service attacks. It seems we hear of such issues on an almost daily basis, and they get scarier as hackers improve their skills.
Of all the challenges, the most important place for organizations to spend their resources is on documenting their identity and access management policy framework, including documenting their organizational roles and the access to be provided to the people within these roles, as this lays the groundwork for better management and automation.
Let Us Solve Your IAM Challenges
Let our team of IT professionals implement robust IAM policies and procedures for your organization.
Challenges in IAM Policies and Compliance Creation
With routine audits, the requirements to provide reports and notify people of breaches will be extremely challenging for certain types of organizations to demonstrate identity and access management compliance. The primary concern in almost every organization remains proving individual access follows policies and tying a person’s identity to their access, especially when access is managed manually. The challenge becomes even more significant when data can be accessed via personal devices and laptops with local hard drives.
 Securing data from external intrusion is also challenging as it requires the ability to secure the data centre, network, and server/application environment. As systems become distributed amongst cloud servers, across multiple internal and externally hosted cloud infrastructure and globally diverse, the identity and access management compliance becomes even more challenging.
Securing data from external intrusion is also challenging as it requires the ability to secure the data centre, network, and server/application environment. As systems become distributed amongst cloud servers, across multiple internal and externally hosted cloud infrastructure and globally diverse, the identity and access management compliance becomes even more challenging.
This leads to organizations wasting valuable resources meeting audit requirements, proving manual controls, monitoring systems for intrusion, and addressing security vulnerabilities and breaches. With as much effort as they are spending, many learn it’s still not enough when they fall prey to ransomware attacks, data breaches, or other denial of service attacks. It seems we hear of such issues on an almost daily basis, and they get scarier as hackers improve their skills.
Of all the challenges, the most important place for organizations to spend their resources is on documenting their identity and access management policy framework, including documenting their organizational roles and the access to be provided to the people within these roles, as this lays the groundwork for better management and automation.
How Automation Solves IAM Compliance Challenges
Automation is key to access and identity management compliance and monitoring. There are several layers in which automation can support an access and identity management policy framework:Provisioning
The standard for provisioning automation is applications that provide access to all systems and applications using single-sign-on (SSO). These applications understand the access to be provided by role and govern the user's ability to sign on, providing access only as authorized. They can also be integrated into HR systems or help desk ticketing systems to automatically provide or revoke access based on onboarding or offboarding activities. Automated provisioning and single-sign-on systems lower the risk of incorrectly provisioned users, providing access to employees unintentionally and lower the audit burden. Rather than having to prove access controls for randomly selected users, IT can show the configuration and policy documentation to provide proof for audits and segregation of duties.
Remote Access
Multi-factor authentication through tokens and/or cell phones before granting network access are pretty standard and used by many organizations to enable workers to access internal resources from home or during travel. These tools can be combined with a virtual desktop environment making sure no data leaves the physical walls of the organization, even in a work-from-home or virtual arrangement.
Intrusion Detections, Monitoring, and Reporting:
Automation is also available on the operations side of the IAM equation:
- Automated network monitoring can track the IPs used to gain access to systems, alerting network managers of potential intrusion or denial of service attacks based on known attack patterns
- Vulnerability management systems can map known vulnerabilities against systems in use, identifying systems that require maintenance activities
- Cloud security suites help prevent attacks in a cloud or managed cloud environment
- Cloud-managed service providers and outsourced managed service providers use automation and can provide reporting on access as needed
CG Technologies – IAM Compliance Process Manager
CG Technologies maintains a rock-solid security practice that makes security a focus for our hosted cloud solutions and managed services but can also help organizations realize their identity and access management compliance goals.
Our IAM Compliance Manager can help you document your identity and access management requirements and build your policy framework by providing expertise, guidance, and templates you need to document your identity and access management policies. We partner with you to ensure your systems and application security is bullet-proof by securing the services we support or provide and by helping you secure access at the application level. Together we can help with all your identity access management compliance needs.